Retrieving data from compact flash drives
Compact flash drives are one of the most commonly used type of mass storage in today s world of technology. The main idea to invent these storage devices was to save large files concerning photos, videos and games. So, the compact flash drives are mainly used in cameras, video recorders, game consoles etc.
Compact flash drives being an electronic device is subjected to various risks. Damage to either the file or the storage device itself can occur naturally or can be due to human errors.
LARGE FILE SIZE
The main reason for data to be at risk is due to its size. We look to save large amount of photos or videos but the quality of the image plays a huge part. Better quality involves taking up more memory than usual. It becomes more complicated when we are recording videos. We do not know the amount of space it consumes and sometimes there is a possibility that media can be incomplete. This phenomenon can lead to files that are corrupt.
VIRUS ATTACKS
CF cards like other storage devices can be targeted by viruses. The only preventive measure is to ensure we have an antivirus software installed when we connect CF cards through an adapter to transfer or save files. The attack of viruses can result in files being corrupted or eventually deleted.
PHYSICAL LIMITATIONS
Another important feature to consider while using Compact flash memory cards is the range of temperature in which it operates. -45 degree Celsius to 85 degrees Celsius. The specific voltage needs to be supplied i.e. 3.3V or 5V. It depends entirely on the type of CF card involved.
ACCIDENTAL REMOVAL OF FILES
This is one of the most common mishaps involved in any storage device. Human damage is the highest percentage. We tend to delete files accidently or try to modify files that can result in loss of data. There is no way of preventing this but we can be cautious by backing up the data.
FORMATING DATA
CF cards are mostly employed in cameras, camcorders etc. We tend to press on the format button by mistake or intentionally which can remove data.
PHYSICAL DAMAGE
There are few storage devices or cameras that use CF card as an internal storage. When it is dropped down or damaged by accident there is a possibility that data =stored on the drive is at risk.
Always remember data that is deleted is not permanently gone until overwriting takes place. The main idea to prevent loss of data is to identify quickly that data is at risk and visit a data recovery specialist.
Visit us at IVITER one of the best teams specializing in Compact flash memory. Have your data serviced in the hands of the world’s best with the highest possible quality.
CONTACT US
PHONE: 22 297 70 40
PHONE2: 731 153 969
ADDRESS: Dzielna 7A (MAP)
E-MAIL: info@iviter.pl
Call us and discuss your case, you don’t have to approach us for recuperation – however, we will readily check what should be possible for your situation. We welcome you for a free analysis and assessment of conceivable recovery.



 Mostly, the concept of server data storage is the involvement of the RAID (Redundant array of in expensive disks). We know how the RAID functions. There could be several reasons for these disks failing.
Mostly, the concept of server data storage is the involvement of the RAID (Redundant array of in expensive disks). We know how the RAID functions. There could be several reasons for these disks failing. Visit us at IVITER, one of the world¡¦s best data recovery organization. We can help you identify the problem associated with the device and can have this fixed with the highest possible quality eventually giving you back your data 100%.
Visit us at IVITER, one of the world¡¦s best data recovery organization. We can help you identify the problem associated with the device and can have this fixed with the highest possible quality eventually giving you back your data 100%.
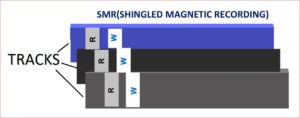 Data is stored in tracks and sectors on the disc. In a normally operating hard disk we see that data is written parallel to each other on data tracks which are closely grouped. This method of operation is termed Perpendicular magnetic recording.
Data is stored in tracks and sectors on the disc. In a normally operating hard disk we see that data is written parallel to each other on data tracks which are closely grouped. This method of operation is termed Perpendicular magnetic recording. Software mainly determines the order in which the operations are executed and which operations should be carried out. It can be referred to the heart of an electronic device.\
Software mainly determines the order in which the operations are executed and which operations should be carried out. It can be referred to the heart of an electronic device.\

 The idea of Steganography was from the historical period dating back to 400 BC, which was used by a king to intimate another country about an attack that was to be carried out. It was written on his servants head and he has his hair grown after that and then was shaved to have the message communicated. This was the base for the term to come into existence. Ever since then there has been so many instances of steganography being observed.
The idea of Steganography was from the historical period dating back to 400 BC, which was used by a king to intimate another country about an attack that was to be carried out. It was written on his servants head and he has his hair grown after that and then was shaved to have the message communicated. This was the base for the term to come into existence. Ever since then there has been so many instances of steganography being observed.